Have you ever wondered if VNC is secure enough for your remote work needs? Well, buckle up because we're diving deep into the world of VNC and uncovering all its secrets. As more people rely on remote connections, understanding the security aspects of VNC is crucial. In this article, we’ll break down everything you need to know about VNC security and help you decide if it’s the right choice for your setup.
Let’s be honest—working remotely has become the norm. Whether you’re managing servers, accessing workstations, or helping a friend troubleshoot their computer, VNC (Virtual Network Computing) has been a go-to tool for years. But here’s the million-dollar question: is VNC secure? The answer isn’t as simple as a yes or no, but don’t worry—we’ll break it down for you in a way that even your grandma could understand.
In today’s digital age, security is everything. From hackers to data breaches, the risks are real. That’s why we’re here to give you the lowdown on VNC security. By the end of this article, you’ll know exactly what makes VNC secure—or not—and how to protect yourself while using it. So, grab a cup of coffee, and let’s get started!
Read also:Kira Kattan The Rising Star Whorsquos Turning Heads In Hollywood
Before we dive into the nitty-gritty details, here’s a quick table of contents to help you navigate through this massive guide:
- What is VNC?
- How Does VNC Work?
- Is VNC Secure?
- Common Security Issues with VNC
- Ways to Enhance VNC Security
- VNC Encryption and Authentication
- Alternatives to VNC
- VNC for Business Use
- Tips for Safe VNC Usage
- Conclusion
What is VNC?
VNC, or Virtual Network Computing, is a remote desktop technology that allows you to control another computer remotely. Think of it as a virtual bridge that connects your device to another, enabling you to see and interact with its screen as if you were sitting right in front of it. VNC is widely used for troubleshooting, remote work, and even teaching purposes.
But here’s the thing—VNC isn’t just one program. It’s a protocol that has been implemented by various software solutions, each with its own features and security measures. Some popular VNC implementations include TightVNC, RealVNC, and UltraVNC. These tools offer different levels of functionality and security, so it’s important to choose the right one for your needs.
Why VNC is Popular
Let’s break down why VNC has become such a popular choice:
- Cross-Platform Support: VNC works on Windows, macOS, Linux, and even mobile devices.
- Simple Setup: Most VNC clients are easy to install and configure, making them accessible to users of all skill levels.
- Customizable: You can tweak settings like screen resolution, color depth, and performance to suit your preferences.
But with great power comes great responsibility. While VNC is powerful, its security is often questioned. Let’s explore why.
How Does VNC Work?
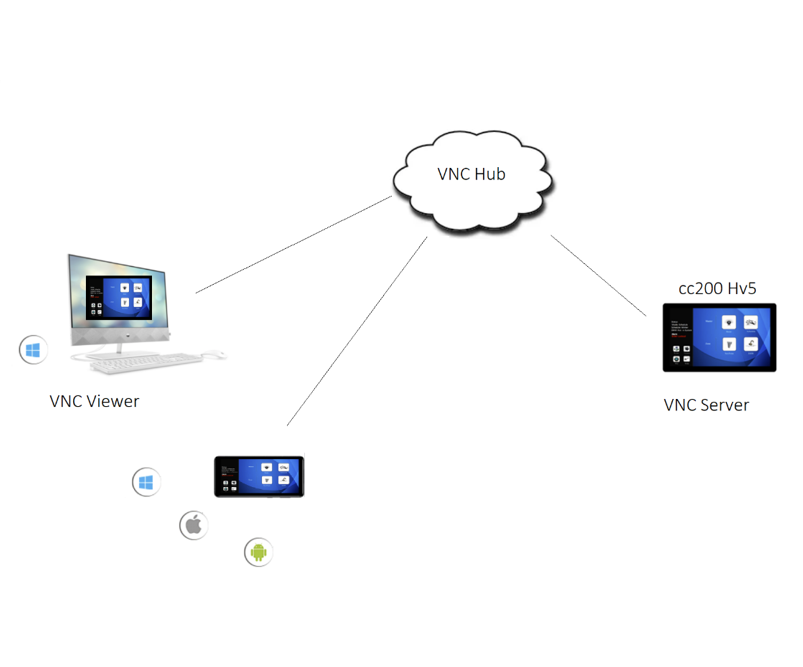
VNC operates on a client-server model. Here’s how it works in simple terms:
Read also:Devon Jenelle Onlyfans The Ultimate Guide To Her Content Journey And Success
- Server Setup: The computer you want to control remotely acts as the VNC server. You’ll need to install and configure the VNC server software on this machine.
- Client Connection: The device you’re using to access the remote computer acts as the VNC client. You’ll install the VNC client software and connect to the server using its IP address or hostname.
- Screen Sharing: Once connected, the VNC client receives screen updates from the server in real-time. You can interact with the remote computer as if you were physically there.
Now, here’s where things get interesting. VNC sends screen updates and input commands over the network, which raises concerns about data privacy and security. Let’s dive deeper into this topic.
Is VNC Secure?
The short answer? It depends. VNC can be secure if used correctly, but it also has vulnerabilities that need to be addressed. Here’s what you need to know:
By default, older versions of VNC didn’t offer strong encryption or authentication mechanisms. This meant that sensitive data, such as passwords and screen updates, could be intercepted by hackers. However, modern VNC implementations have improved significantly in terms of security.
Key Security Features in VNC
Here are some of the security features you can expect from most VNC solutions:
- Encryption: Many VNC clients now support SSL/TLS encryption to protect data in transit.
- Authentication: Password protection and user authentication help ensure only authorized users can access the remote computer.
- Firewall Integration: Some VNC solutions work seamlessly with firewalls to enhance security.
But as we’ll see in the next section, there are still potential risks to be aware of.
Common Security Issues with VNC
While VNC has come a long way in terms of security, there are still some common issues that users should be aware of:
- Weak Passwords: Using simple or easily guessable passwords can make your VNC connection vulnerable to brute-force attacks.
- Lack of Encryption: If encryption isn’t enabled, sensitive data can be intercepted by attackers.
- Unpatched Software: Failing to update your VNC software can leave you exposed to known vulnerabilities.
These issues highlight the importance of taking proactive steps to enhance VNC security. Let’s explore some ways to do that.
Ways to Enhance VNC Security
Here are some practical tips to make your VNC connections more secure:
1. Use Strong Passwords: Avoid using easily guessable passwords. Instead, opt for complex combinations of letters, numbers, and symbols.
2. Enable Encryption: Make sure encryption is enabled in your VNC settings. This will protect your data from being intercepted during transmission.
3. Regularly Update Software: Keep your VNC client and server software up to date to protect against known vulnerabilities.
4. Restrict Access: Limit who can access your VNC server by setting up IP whitelisting or using a firewall.
Advanced Security Measures
For those who need extra security, consider these advanced measures:
- Two-Factor Authentication (2FA): Add an extra layer of security by requiring a second form of verification, such as a text message or authentication app.
- Use a Virtual Private Network (VPN): A VPN can encrypt all traffic between your devices, adding an additional layer of protection.
By implementing these measures, you can significantly reduce the risks associated with VNC.
VNC Encryption and Authentication
Encryption and authentication are two of the most important aspects of VNC security. Here’s how they work:
Encryption: This process converts your data into a code that can only be read by someone with the correct decryption key. Most modern VNC solutions use SSL/TLS encryption to protect data in transit.
Authentication: This ensures that only authorized users can access the remote computer. VNC typically uses password-based authentication, but some implementations also support more advanced methods like public key authentication.
Both encryption and authentication are crucial for maintaining the security of your VNC connections. Without them, your data could be vulnerable to interception or unauthorized access.
Alternatives to VNC
If VNC doesn’t meet your security needs, there are several alternatives you can consider:
- TeamViewer: A popular remote desktop solution that offers strong encryption and easy setup.
- Remote Desktop Protocol (RDP): A Microsoft-developed protocol that provides robust security features.
- AnyDesk: A lightweight remote desktop tool that focuses on speed and security.
Each of these alternatives has its own strengths and weaknesses, so it’s important to evaluate them based on your specific requirements.
VNC for Business Use
For businesses, VNC can be a powerful tool for managing remote workstations and servers. However, it’s essential to implement proper security measures to protect sensitive company data.
Here are some best practices for using VNC in a business environment:
- Set Up a Centralized Management System: Use a centralized tool to manage all VNC connections and monitor activity.
- Enforce Strict Access Controls: Limit who can access VNC servers and implement role-based permissions.
- Regularly Audit Logs: Keep an eye on VNC activity logs to detect any suspicious behavior.
By following these best practices, businesses can safely leverage VNC for remote access and management.
Tips for Safe VNC Usage
Here are some final tips to ensure safe VNC usage:
1. Educate Users: Make sure everyone who uses VNC understands the importance of security and follows best practices.
2. Test Your Setup: Regularly test your VNC configuration to ensure it’s working as intended and doesn’t have any security gaps.
3. Backup Data: Always keep backups of important data to prevent loss in case of a security breach.
By following these tips, you can enjoy the benefits of VNC while minimizing the risks.
Conclusion
So, is VNC secure? The answer is a resounding yes—if you take the necessary precautions. Modern VNC implementations offer robust security features, but it’s up to you to configure them properly and stay vigilant against potential threats.
Here’s a quick recap of what we’ve covered:
- VNC is a powerful remote desktop technology with cross-platform support.
- While VNC can be secure, it’s important to address common vulnerabilities like weak passwords and lack of encryption.
- By enabling encryption, using strong passwords, and regularly updating your software, you can enhance VNC security.
- For businesses, implementing centralized management and strict access controls is crucial for safe VNC usage.
Now that you know the ins and outs of VNC security, it’s time to take action. Whether you’re using VNC for personal or professional purposes, make sure to follow the tips and best practices outlined in this article. And don’t forget to share your thoughts in the comments below—we’d love to hear from you!