Hey there, tech-savvy friend! Ever heard of VNC Viewer? Well, buckle up because we're diving deep into its security vulnerabilities that could leave your system exposed. In today's interconnected world, remote access tools like VNC Viewer are essential for productivity—but they come with risks you need to understand. This article will break it all down for you, so you can stay safe while staying connected.
VNC Viewer has been a game-changer for remote work, IT support, and collaborative projects. But let's not forget that with great power comes great responsibility. Security vulnerabilities in VNC Viewer could compromise sensitive data, and no one wants their personal or business information floating around the dark web, right? That's why understanding these risks is crucial.
We'll explore everything from common VNC Viewer security vulnerabilities to practical tips for protecting yourself. Whether you're a seasoned IT pro or just someone trying to keep their home network safe, this guide will arm you with the knowledge you need. Let's get started!
Read also:Kira Kattan The Rising Star Whorsquos Turning Heads In Hollywood
Table of Contents
- What is VNC Viewer?
- Common VNC Viewer Security Vulnerabilities
- A Brief History of VNC
- Impact on Businesses
- How to Protect Your System
- Best Practices for VNC Security
- Data Encryption in VNC
- Firewall Settings for VNC
- User Authentication and Access Control
- Future Directions for VNC Security
What is VNC Viewer?
Let's start with the basics. VNC (Virtual Network Computing) Viewer is a powerful remote desktop tool that allows you to access and control another computer over a network. Think of it as a digital key that lets you unlock doors to faraway computers. It's widely used by IT professionals, remote workers, and even tech-savvy individuals for troubleshooting, collaboration, and convenience.
But here's the kicker: VNC Viewer isn't just about convenience. It's also about security—or lack thereof, if not properly configured. The tool itself is great, but its vulnerabilities can be exploited by hackers who are always on the lookout for weak points in your system.
A Quick Overview
- VNC Viewer lets you remotely control another computer.
- It's widely used in businesses and personal settings.
- Security vulnerabilities can lead to serious consequences.
Common VNC Viewer Security Vulnerabilities
Alright, let's talk about the elephant in the room: VNC Viewer security vulnerabilities. These flaws can range from weak authentication methods to unencrypted data transfers. Here are some of the most common issues you should be aware of:
Weak Passwords
One of the biggest culprits is weak passwords. If you're still using "password123" or "qwerty," you're basically rolling out the red carpet for hackers. Strong, unique passwords are your first line of defense, so make sure you're not cutting corners here.
Unencrypted Connections
Another biggie is unencrypted connections. Without encryption, your data is like an open book for anyone who intercepts it. It's like shouting your secrets in a crowded room. Encryption ensures that even if someone intercepts your data, they won't be able to make sense of it.
Outdated Software
Using outdated software is another common pitfall. Developers are constantly patching vulnerabilities, so failing to update your VNC Viewer can leave you exposed to known exploits. Always keep your software up to date, folks!
Read also:Unveiling Myla Del Rey The Rising Star On Onlyfans
A Brief History of VNC
Before we dive deeper, let's take a quick trip down memory lane. VNC was originally developed at AT&T Laboratories Cambridge in the late 1990s. The goal was simple: create a platform-independent remote desktop tool that could work across different operating systems. And boy, did they succeed!
VNC has since evolved into a family of tools, with various implementations and features. Today, it's one of the most widely used remote access solutions, powering everything from corporate IT departments to home users tinkering with their Raspberry Pi setups.
VNC Timeline
- 1990s: VNC is developed at AT&T Laboratories Cambridge.
- 2000s: VNC gains popularity in corporate and personal settings.
- 2010s: VNC evolves with new features and security enhancements.
Impact on Businesses
Now, let's talk about the impact of VNC Viewer security vulnerabilities on businesses. For companies, the stakes are higher than ever. A single breach can lead to data loss, financial damage, and reputational harm. Here's how:
Data Breaches
Data breaches are a nightmare for any business. If a hacker gains access to your VNC Viewer, they could steal sensitive information, including customer data, financial records, and trade secrets. This not only costs money but can also erode customer trust.
Financial Loss
Financial loss is another big concern. Breaches often lead to legal fees, fines, and compensation payments. Plus, there's the cost of fixing the damage and implementing new security measures. It's a pricey headache no one wants to deal with.
Reputational Damage
Finally, there's reputational damage. In today's competitive market, trust is everything. A security breach can tarnish your brand's image and make customers think twice before doing business with you. Protecting your reputation is just as important as protecting your data.
How to Protect Your System
So, how do you protect your system from VNC Viewer security vulnerabilities? It's all about taking proactive steps to secure your setup. Here are some practical tips:
Use Strong Passwords
As we mentioned earlier, strong passwords are key. Use a mix of uppercase and lowercase letters, numbers, and symbols. And don't reuse passwords across different accounts. A password manager can help keep track of all your complex passwords.
Enable Encryption
Encryption is your best friend when it comes to securing VNC connections. Make sure encryption is enabled in your VNC Viewer settings. This will protect your data from prying eyes and ensure that even if someone intercepts it, they won't be able to read it.
Keep Software Updated
Regularly updating your software is crucial. Developers are constantly patching vulnerabilities, so staying up to date ensures you have the latest security features. Set up automatic updates if possible, so you don't have to worry about missing a patch.
Best Practices for VNC Security
Beyond the basics, there are some best practices you can follow to further enhance your VNC security:
Limit Access
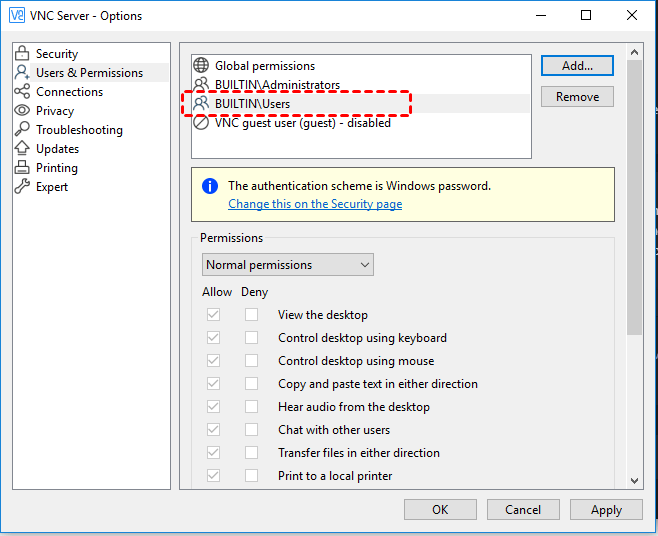
Only grant access to trusted users. Use role-based access control to ensure that each user has the minimum level of access they need to perform their tasks. This reduces the risk of unauthorized access.
Monitor Activity
Regularly monitor VNC activity for any suspicious behavior. Set up alerts for unusual login attempts or unauthorized access. This way, you can quickly respond to potential threats before they escalate.
Use a Firewall
A firewall is another layer of protection that can help block unauthorized access. Configure your firewall to only allow VNC connections from trusted IP addresses. This adds an extra layer of security to your setup.
Data Encryption in VNC
Let's talk more about data encryption in VNC. Encryption is the process of converting data into a code to prevent unauthorized access. In VNC, encryption can be implemented at different levels, including transport layer security (TLS) and SSH tunneling.
Transport Layer Security (TLS)
TLS is a protocol that provides secure communication over a network. When used with VNC, it encrypts the data being transmitted between the client and server, making it much harder for hackers to intercept and read.
SSH Tunneling
SSH tunneling is another method of securing VNC connections. It works by encapsulating VNC traffic within an SSH connection, providing an additional layer of encryption. This is especially useful for securing VNC connections over untrusted networks.
Firewall Settings for VNC
Firewall settings are crucial for securing VNC connections. A firewall acts as a barrier between your network and the outside world, controlling which traffic is allowed in and out. Here's how you can configure your firewall for VNC:
Allow Trusted IPs
Configure your firewall to only allow VNC connections from trusted IP addresses. This reduces the risk of unauthorized access and ensures that only legitimate users can connect to your system.
Block Unnecessary Ports
Make sure to block any unnecessary ports that could be used for VNC connections. This minimizes the attack surface and makes it harder for hackers to exploit vulnerabilities.
User Authentication and Access Control
User authentication and access control are critical components of VNC security. They ensure that only authorized users can access your system and limit the level of access they have. Here's how you can implement them:
Two-Factor Authentication
Two-factor authentication (2FA) adds an extra layer of security by requiring users to provide two forms of identification before accessing the system. This could be a password and a one-time code sent to their phone, for example.
Role-Based Access Control
Role-based access control (RBAC) assigns specific roles to users, each with its own set of permissions. This ensures that users only have access to the resources they need to perform their tasks, reducing the risk of unauthorized access.
Future Directions for VNC Security
As technology continues to evolve, so do the methods used to secure VNC connections. Here are some future directions for VNC security:
AI-Driven Security
Artificial intelligence (AI) is increasingly being used to enhance security systems. In the future, AI could be used to detect and respond to VNC security threats in real time, providing a more proactive approach to security.
Quantum Encryption
Quantum encryption is a cutting-edge technology that uses the principles of quantum mechanics to secure data. While still in its infancy, it has the potential to revolutionize data security, including VNC connections.
And there you have it, folks! A comprehensive guide to VNC Viewer security vulnerabilities and how to protect yourself. Remember, staying safe in the digital world requires constant vigilance and proactive measures. By following the tips and best practices outlined in this article, you can enjoy the convenience of VNC Viewer without compromising your security.
Kesimpulan
To wrap things up, VNC Viewer is an invaluable tool for remote access, but it comes with its own set of security challenges. From weak passwords to unencrypted connections, the vulnerabilities are real and can have serious consequences. However, by taking the right precautions, such as using strong passwords, enabling encryption, and keeping your software updated, you can significantly reduce the risk.
We encourage you to share this article with your friends and colleagues who use VNC Viewer. The more people know about these security risks, the safer we all are. And don't forget to leave a comment below if you have any questions or tips of your own. Let's keep the conversation going and stay secure together!