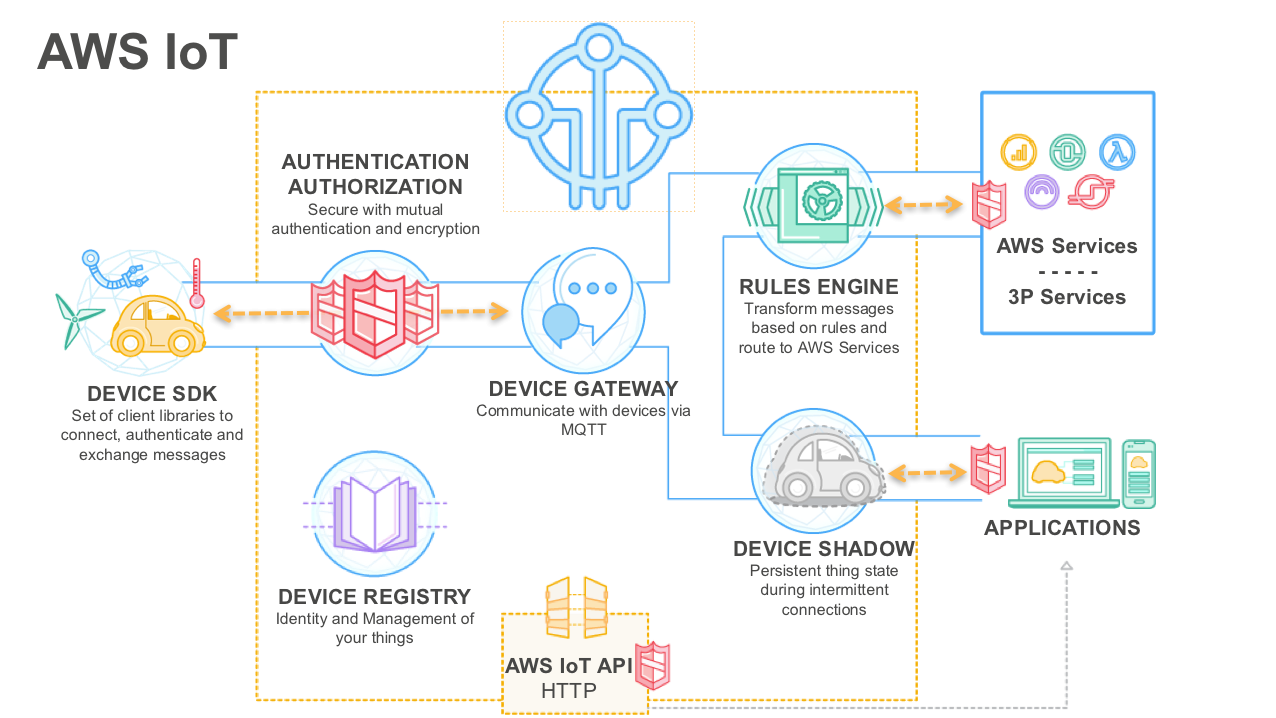
So, you're here because you want to dive deep into the world of IoT SSH access devices on AWS, right? Well, buckle up, my friend, because we're about to take a thrilling ride through the realm of secure connectivity. Whether you're a tech enthusiast, a developer, or just someone curious about how IoT devices can integrate seamlessly with AWS, this article has got you covered. IoT SSH access device AWS is more than just a buzzword—it’s the future of secure communication in the digital age.
Now, let's face it: securing your IoT devices is no longer optional. With hackers lurking around every corner of the internet, it’s crucial to have a robust system in place. That’s where SSH (Secure Shell) comes into play. Think of SSH as the superhero of secure connections, protecting your data like a fortress. And when you combine it with AWS, you’re talking about a powerhouse duo that can revolutionize the way you manage your IoT infrastructure.
But hold up, before we get too far ahead of ourselves, let’s break this down. This article isn’t just about throwing jargon at you. We’re here to make sure you understand the ins and outs of IoT SSH access devices on AWS, why they matter, and how you can implement them in your projects. So, whether you’re a beginner or a seasoned pro, there’s something here for everyone. Let’s jump in!
Read also:Unveiling The Life Of Jyoti Amge And Her Husband A Journey Through Love And Challenges
What Exactly is an IoT SSH Access Device?
Alright, let’s start with the basics. An IoT SSH access device is essentially a tool or hardware that allows you to remotely connect to your IoT devices using the Secure Shell protocol. Think of it as a secure tunnel that lets you control your devices from anywhere in the world without worrying about unauthorized access. And when you add AWS to the mix, you’re talking about cloud-based scalability and reliability that can handle even the most demanding IoT projects.
Here’s why this matters: traditional methods of accessing IoT devices often come with security risks. You could expose your network to potential breaches or leave sensitive data vulnerable. With SSH, you encrypt your connections, ensuring that only authorized users can access your devices. It’s like having a digital bouncer at the door, making sure no one gets in without the proper credentials.
Why AWS is the Perfect Partner for IoT SSH Access
Now, let’s talk about AWS. Amazon Web Services isn’t just another cloud provider; it’s the gold standard for scalability, security, and innovation. When you pair AWS with your IoT SSH access devices, you’re tapping into a massive ecosystem of tools and services that can help you build, deploy, and manage your IoT infrastructure with ease.
AWS offers features like AWS IoT Core, which allows you to securely interact with billions of devices. It also integrates seamlessly with other AWS services, such as Lambda and S3, giving you the flexibility to create custom solutions tailored to your needs. Plus, with AWS’s global infrastructure, you can rest assured that your devices will always be connected, no matter where they are in the world.
Top IoT SSH Access Devices for AWS Integration
So, which devices should you consider when setting up your IoT SSH access on AWS? Here’s a list of some of the best options available today:
- Raspberry Pi: A popular choice for hobbyists and professionals alike, the Raspberry Pi is a versatile device that can be easily configured for SSH access. Plus, it’s super affordable!
- NVIDIA Jetson Nano: If you’re looking for something with a bit more power, the Jetson Nano is a great option. It’s perfect for AI-driven IoT projects and offers excellent performance.
- ESP32: This tiny yet powerful microcontroller is ideal for low-power IoT applications. It supports Wi-Fi and Bluetooth, making it easy to integrate with AWS.
- BeagleBone Black: Another popular choice, the BeagleBone Black is known for its ease of use and compatibility with various Linux distributions.
Choosing the Right Device for Your Needs
When selecting an IoT SSH access device for AWS, it’s important to consider factors like performance, power consumption, and ease of integration. For example, if you’re working on a large-scale project, you might want to go with something like the NVIDIA Jetson Nano for its processing power. On the other hand, if you’re just starting out, the Raspberry Pi could be the perfect entry-level option.
Read also:Francesca Farago Onlyfans Leak What You Need To Know About The Controversy
Setting Up SSH Access on AWS
Now that you’ve got your device, let’s talk about setting up SSH access on AWS. The process is relatively straightforward, but there are a few key steps you’ll need to follow:
- Create an EC2 instance on AWS and configure it for SSH access.
- Generate an SSH key pair and download the private key to your local machine.
- Connect to your EC2 instance using an SSH client, such as PuTTY or Terminal.
- Configure your IoT device to connect to the EC2 instance via SSH.
Once you’ve completed these steps, you’ll have a secure connection between your IoT device and AWS. It’s like building a digital bridge that allows you to manage your devices from anywhere in the world.
Security Best Practices for IoT SSH Access
Security should always be top of mind when working with IoT devices. Here are a few best practices to keep your SSH connections secure:
- Use strong passwords: Avoid using common passwords or ones that are easy to guess. Consider using a password manager to generate and store complex passwords.
- Enable two-factor authentication: Adding an extra layer of security can go a long way in preventing unauthorized access.
- Regularly update your devices: Keep your firmware and software up to date to patch any vulnerabilities.
- Monitor your connections: Use tools like AWS CloudWatch to monitor your SSH connections and detect any suspicious activity.
Common Security Threats to Watch Out For
While SSH is a secure protocol, it’s not completely immune to threats. Some common vulnerabilities to watch out for include brute-force attacks, man-in-the-middle attacks, and unauthorized key access. By following the best practices outlined above, you can significantly reduce the risk of these threats.
Cost Considerations for IoT SSH Access on AWS
Let’s talk money. While AWS offers a ton of great features, it’s important to keep an eye on your budget. AWS pricing can vary depending on the services you use and the resources you consume. For example, running an EC2 instance for SSH access might cost you a few dollars per month, while using AWS IoT Core could incur additional charges based on the number of messages processed.
To keep costs under control, consider using AWS’s free tier for testing and development. This allows you to experiment with AWS services without breaking the bank. Additionally, make sure to shut down any unused resources to avoid unnecessary charges.
Tips for Managing Costs
Here are a few tips for managing costs when working with IoT SSH access on AWS:
- Use AWS Cost Explorer to track your spending and identify areas where you can save.
- Optimize your resource usage by scaling up or down as needed.
- Take advantage of AWS’s reserved instances for long-term projects.
Real-World Applications of IoT SSH Access Devices on AWS
So, how are companies actually using IoT SSH access devices on AWS? Here are a few real-world examples:
- Smart Agriculture: Farmers are using IoT devices to monitor soil moisture levels and automate irrigation systems. SSH access allows them to remotely manage these devices and make data-driven decisions.
- Remote Healthcare: Medical facilities are leveraging IoT devices for remote patient monitoring. SSH ensures that sensitive patient data is transmitted securely over the internet.
- Smart Cities: Cities are using IoT devices to monitor traffic patterns, air quality, and energy usage. SSH access enables city officials to manage these devices from a central location.
Future Trends in IoT SSH Access on AWS
The future of IoT SSH access on AWS looks bright. As more and more devices become connected, the demand for secure and scalable solutions will only increase. Some trends to watch out for include:
- Edge Computing: By processing data closer to the source, edge computing can reduce latency and improve performance for IoT devices.
- Artificial Intelligence: AI-powered IoT devices can analyze data in real-time, providing insights that can drive better decision-making.
- Quantum Computing: While still in its early stages, quantum computing has the potential to revolutionize the way we secure IoT devices and manage SSH connections.
Preparing for the Future
To stay ahead of the curve, it’s important to keep learning and adapting to new technologies. Consider taking online courses or attending industry conferences to stay up-to-date with the latest trends in IoT and cloud computing. And don’t be afraid to experiment with new tools and services to see what works best for your projects.
Conclusion
And there you have it, folks—a comprehensive guide to the best IoT SSH access devices on AWS. From understanding the basics to setting up secure connections and exploring real-world applications, we’ve covered it all. IoT SSH access device AWS isn’t just a fancy term; it’s a game-changer for anyone looking to secure their IoT infrastructure.
Before you go, I’d love to hear your thoughts. Have you worked with IoT SSH access devices on AWS before? What challenges have you faced, and how did you overcome them? Drop a comment below and let’s keep the conversation going. And don’t forget to share this article with your friends and colleagues who might find it useful. Together, let’s build a safer, smarter, and more connected world!
Table of Contents
- What Exactly is an IoT SSH Access Device?
- Why AWS is the Perfect Partner for IoT SSH Access
- Top IoT SSH Access Devices for AWS Integration
- Choosing the Right Device for Your Needs
- Setting Up SSH Access on AWS
- Security Best Practices for IoT SSH Access
- Common Security Threats to Watch Out For
- Cost Considerations for IoT SSH Access on AWS
- Tips for Managing Costs
- Real-World Applications of IoT SSH Access Devices on AWS