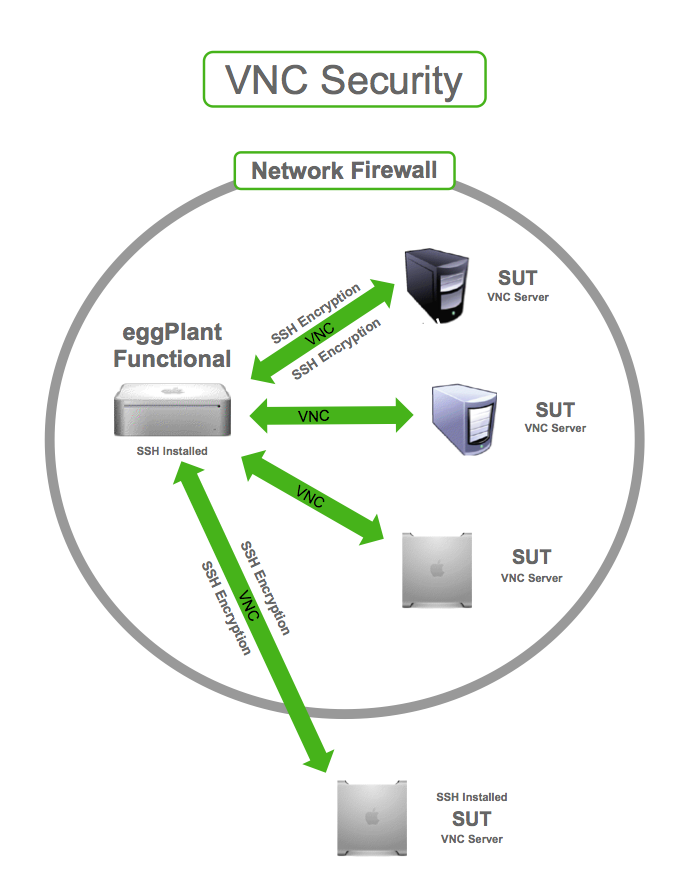
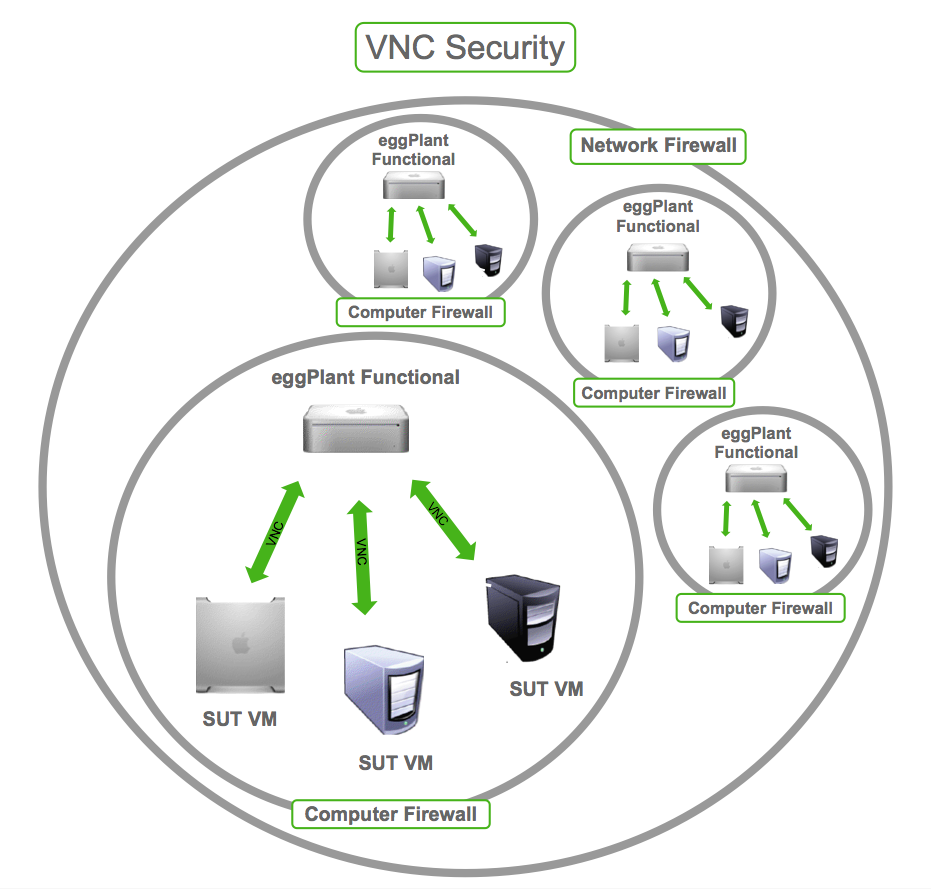
So, let's talk about VNC security flaws, shall we? You might be thinking, "What's the big deal with VNC anyway?" Well, Virtual Network Computing (VNC) is a powerful tool that lets you remotely control another computer, but it's not without its risks. Imagine this: you're sitting at your desk, sipping your coffee, and suddenly someone else has access to your system. Scary, right? That's why understanding VNC security flaws is crucial for anyone using this technology.
Whether you're a business owner, a tech enthusiast, or just someone who likes to tinker with computers, VNC can be a game-changer. But, like any technology, it has vulnerabilities that can be exploited by hackers. In this article, we'll dive deep into the world of VNC security flaws, exploring what they are, how they work, and most importantly, how you can protect yourself.
Before we get into the nitty-gritty, let me give you a heads up. This isn't just another tech article. We're going to break it down in a way that's easy to understand, with real-world examples and actionable tips. By the time you're done reading, you'll have a solid understanding of VNC security flaws and how to keep your system safe. So, grab a snack, settle in, and let's get started!
Read also:Eevieaspen Of Leaks Unraveling The Truth Behind The Curtain
Understanding VNC and Its Security Risks
VNC, or Virtual Network Computing, is like a digital key that lets you unlock and control another computer from afar. It's been around for a while now and has become a staple in many industries. But with great power comes great responsibility, and in this case, that responsibility is all about security. VNC security flaws are real, and they can have serious consequences if left unchecked.
What Exactly is VNC?
VNC is a remote desktop protocol that allows users to remotely control another computer. It works by sending keyboard and mouse events from one computer to another, along with screen updates in the other direction. Think of it as a digital handshake that lets two computers communicate and work together seamlessly.
However, this convenience comes at a price. VNC security flaws can make your system vulnerable to attacks. Hackers can exploit these flaws to gain unauthorized access to your computer, steal sensitive data, or even take control of your system entirely. It's a scary thought, but one that we need to take seriously.
Common VNC Security Flaws
Now that we know what VNC is, let's take a look at some of the most common VNC security flaws. These vulnerabilities can leave your system wide open to attacks if you're not careful. Here are a few of the biggest culprits:
- Weak Passwords: Using simple or easily guessable passwords is one of the biggest mistakes people make when setting up VNC. Hackers can use brute-force attacks to crack these passwords in no time.
- Outdated Software: Failing to keep your VNC software up to date can leave you exposed to known vulnerabilities. Hackers are always on the lookout for outdated systems that they can exploit.
- Unencrypted Connections: Without encryption, your data is sent in plain text, making it easy for hackers to intercept and read. This can lead to data breaches and other security issues.
- Default Settings: Many people don't bother changing the default settings on their VNC software, which can leave them vulnerable to attacks. Hackers know these default settings and can use them to gain access to your system.
How Hackers Exploit VNC Security Flaws
So, how do hackers actually exploit these VNC security flaws? Well, they have a variety of tools and techniques at their disposal. Here's a look at some of the most common methods:
Brute-Force Attacks
A brute-force attack is when a hacker uses a program to try every possible combination of characters until they find the right password. If you're using a weak or easily guessable password, this process can be surprisingly quick. That's why it's so important to use strong, complex passwords for your VNC connections.
Read also:Francesca Farago Onlyfans Leak What You Need To Know About The Controversy
Man-in-the-Middle Attacks
In a man-in-the-middle attack, a hacker intercepts and potentially alters the communication between two parties. If your VNC connection isn't encrypted, a hacker can easily intercept your data and gain access to your system. This is why using encryption is so crucial when setting up VNC.
Protecting Yourself from VNC Security Flaws
Now that we know what the risks are, let's talk about how you can protect yourself from VNC security flaws. There are several steps you can take to secure your VNC connections and keep your system safe from hackers.
Use Strong Passwords
One of the simplest and most effective ways to protect yourself is to use strong, complex passwords for your VNC connections. A strong password should be at least 12 characters long and include a mix of uppercase and lowercase letters, numbers, and special characters. Avoid using easily guessable information like your name or birthdate.
Enable Encryption
Encrypting your VNC connections is another crucial step in protecting your system. Encryption ensures that your data is sent securely, making it much harder for hackers to intercept and read. Most VNC software offers encryption options, so be sure to enable them when setting up your connections.
Keep Your Software Updated
Regularly updating your VNC software is essential for staying protected against known vulnerabilities. Software updates often include security patches that fix these vulnerabilities, so keeping your software up to date is one of the best ways to protect yourself.
Advanced Security Measures
For those who want to take their VNC security to the next level, there are several advanced measures you can implement. These may require a bit more technical know-how, but they can significantly enhance the security of your VNC connections.
Use Two-Factor Authentication
Two-factor authentication (2FA) adds an extra layer of security to your VNC connections by requiring a second form of verification in addition to your password. This could be something like a code sent to your phone or a biometric scan. While it may seem like an extra step, 2FA can make a huge difference in protecting your system.
Limit Access
Another way to enhance your VNC security is to limit access to only those who absolutely need it. This can be done by setting up user permissions and restricting access to specific IP addresses or networks. By limiting access, you reduce the risk of unauthorized users gaining access to your system.
Real-World Examples of VNC Security Breaches
To give you a better understanding of the potential risks, let's take a look at some real-world examples of VNC security breaches. These stories highlight the importance of taking VNC security seriously and implementing the right measures to protect your system.
The Target Breach
In 2013, Target suffered a massive data breach that compromised the personal information of millions of customers. The hackers gained access to Target's system through a VNC connection that hadn't been properly secured. This breach cost Target millions of dollars and damaged their reputation, serving as a stark reminder of the importance of VNC security.
The WannaCry Ransomware Attack
In 2017, the WannaCry ransomware attack spread rapidly across the globe, infecting hundreds of thousands of computers. One of the ways the malware spread was through unsecured VNC connections. This attack highlighted the need for robust VNC security measures to prevent similar incidents in the future.
Best Practices for VNC Security
Now that we've covered the basics and some advanced measures, let's talk about some best practices for VNC security. These are the things you should be doing on a regular basis to keep your system safe:
- Use strong, unique passwords for each VNC connection.
- Enable encryption for all VNC connections.
- Keep your VNC software up to date with the latest security patches.
- Limit access to only those who need it.
- Implement two-factor authentication wherever possible.
- Regularly monitor your VNC connections for any suspicious activity.
Future Trends in VNC Security
As technology continues to evolve, so too do the methods used to secure VNC connections. Here are a few trends to keep an eye on in the world of VNC security:
AI and Machine Learning
AI and machine learning are increasingly being used to detect and prevent security threats. These technologies can analyze patterns and behaviors to identify potential threats before they become a problem. As they become more advanced, they could play a major role in enhancing VNC security.
Zero Trust Architecture
Zero trust architecture is a security model that assumes no user or device should be trusted by default. Instead, every access request must be verified before being granted. This approach could significantly improve VNC security by ensuring that only authorized users can access your system.
Conclusion
And there you have it, folks. VNC security flaws are a real threat, but with the right knowledge and tools, you can protect yourself and your system from potential attacks. Remember, the key is to stay informed, stay vigilant, and take action to secure your VNC connections. Whether it's using strong passwords, enabling encryption, or implementing advanced security measures, there are plenty of ways to keep your system safe.
So, what are you waiting for? Take a moment to review your VNC setup and make sure you're doing everything you can to protect yourself. And don't forget to share this article with your friends and colleagues so they can stay safe too. Together, we can make the digital world a safer place for everyone.
Table of Contents
![[2025] Fixed! VNC's "Too Many Security Failures" Error](https://images.airdroid.com/2024/09/how-to-fix-vnc-too-many-security-failures-02-768x548.png)