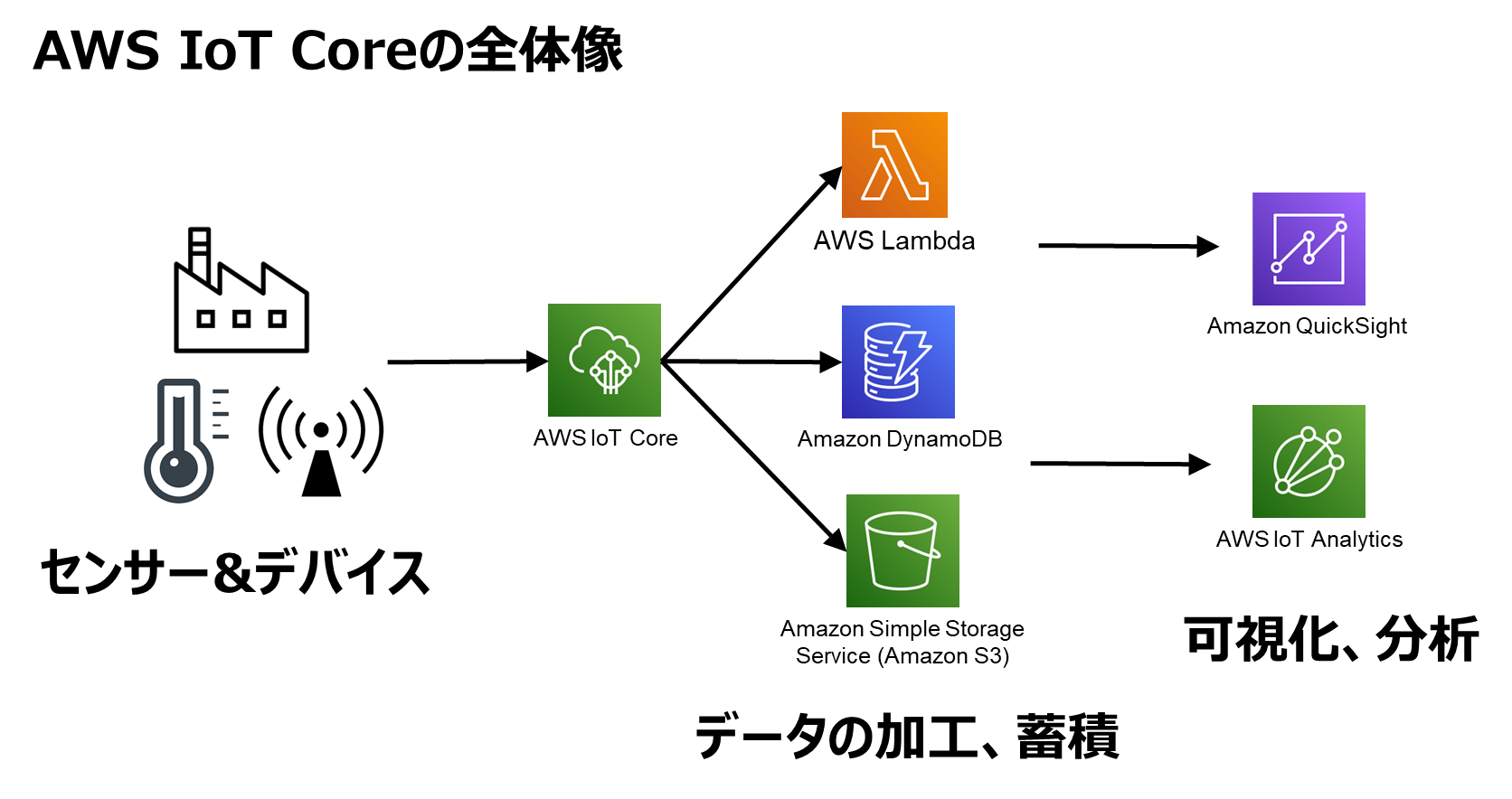
Hey there, tech enthusiasts! If you're diving into the world of IoT (Internet of Things) and cloud computing, you're in for a treat. IoT SSH access on AWS is more than just a buzzword; it's a game-changer for managing devices securely and efficiently. Whether you're a developer, an IT admin, or someone curious about the tech world, this guide will help you understand how SSH access works within AWS's ecosystem. So, buckle up and let's dive into the nitty-gritty!
Now, you might be wondering, "What exactly does IoT SSH access on AWS mean?" Well, it's essentially about securely connecting to your IoT devices through SSH (Secure Shell) using Amazon Web Services. This setup allows you to manage, monitor, and troubleshoot your devices remotely, ensuring they're always up and running without compromising on security.
In today's fast-paced digital world, where connectivity is king, having a robust and secure way to manage your IoT devices is crucial. AWS offers a powerful platform that enables seamless integration and secure access, making it easier than ever to manage your IoT fleet. So, whether you're building a smart home, monitoring industrial equipment, or running a large-scale IoT deployment, this guide will walk you through everything you need to know.
Read also:Eevie Aspenleaks The Untold Story Thats Got Everyone Talking
Table of Contents
- Introduction to IoT SSH on AWS
- Benefits of Using SSH on AWS
- Security Measures in IoT SSH
- Setting Up SSH on AWS
- Common SSH Commands for IoT
- Troubleshooting SSH Issues
- Best Practices for IoT SSH
- Real-World Applications
- Future of IoT SSH on AWS
- Conclusion
Introduction to IoT SSH on AWS
Alright, let's break it down. IoT SSH access on AWS is all about securely connecting to your IoT devices using SSH, a network protocol that encrypts data between two systems. AWS provides the infrastructure and tools to make this process smooth and secure. From setting up your environment to managing your devices, AWS has got you covered.
Why Choose AWS for IoT SSH Access?
Here’s the deal: AWS offers a ton of benefits for managing IoT devices. With features like AWS IoT Core, you can easily connect, monitor, and manage your devices at scale. Plus, AWS's robust security measures ensure that your data remains safe from prying eyes.
Some key reasons to choose AWS include:
- Scalability: AWS can handle thousands of devices without breaking a sweat.
- Security: Advanced encryption and authentication protocols keep your data secure.
- Integration: Seamless integration with other AWS services makes managing your IoT ecosystem a breeze.
Benefits of Using SSH on AWS
Using SSH on AWS for IoT devices offers a bunch of advantages that make it a no-brainer for many organizations. Let’s take a closer look at some of these benefits:
Enhanced Security
Security is a top priority when it comes to IoT devices. SSH provides a secure channel for communication, ensuring that your data remains protected from unauthorized access. AWS enhances this security with features like IAM roles and policies, giving you granular control over who can access your devices.
Remote Access
With SSH, you can access your IoT devices from anywhere in the world. This remote access capability is a huge advantage, especially for large-scale deployments where devices are spread across different locations.
Read also:Devon Jenelle Onlyfans The Ultimate Guide To Her Content Journey And Success
Efficient Management
Managing a fleet of IoT devices can be a daunting task. SSH simplifies this process by allowing you to perform tasks like software updates, configuration changes, and troubleshooting remotely. AWS's management tools further streamline this process, making it easier to keep your devices running smoothly.
Security Measures in IoT SSH
Security is paramount when it comes to IoT SSH access on AWS. Here are some of the key security measures you should consider:
Authentication and Authorization
Using strong authentication mechanisms is crucial. AWS offers features like IAM roles and policies that allow you to control who can access your devices. Additionally, using public and private key pairs for SSH authentication adds an extra layer of security.
Encryption
All communication between your devices and AWS should be encrypted to prevent data interception. SSH uses encryption protocols like AES and RSA to secure your data in transit.
Network Security
Implementing network security measures like firewalls and VPCs (Virtual Private Clouds) can help protect your devices from unauthorized access. AWS provides tools to configure these security measures easily.
Setting Up SSH on AWS
Setting up SSH access for your IoT devices on AWS might sound intimidating, but it's actually pretty straightforward. Here's a step-by-step guide to get you started:
Step 1: Create an EC2 Instance
First, you'll need to create an EC2 instance on AWS. This instance will act as your gateway for accessing your IoT devices via SSH. Make sure to select a security group that allows SSH access.
Step 2: Configure Security Settings
Once your EC2 instance is up and running, configure the security settings to allow SSH access from your IP address. This ensures that only authorized users can connect to your instance.
Step 3: Connect to Your IoT Devices
With your EC2 instance set up, you can now connect to your IoT devices using SSH. Use the public IP address of your instance and your private key to establish the connection.
Common SSH Commands for IoT
Here are some common SSH commands that you'll likely use when managing your IoT devices:
ssh user@ip_address: Connect to your device using SSH.scp file user@ip_address:/path/to/destination: Transfer files to your device.sudo apt update: Update your device's software packages.sudo reboot: Restart your device remotely.
Troubleshooting SSH Issues
Even with the best setup, things can go wrong. Here are some common SSH issues and how to troubleshoot them:
Connection Refused
If you're getting a "connection refused" error, check your security group settings to ensure that SSH access is allowed. Also, verify that your device is running and that the SSH service is active.
Authentication Failed
Authentication issues can occur if your private key is incorrect or if the permissions on your key file are too open. Make sure your key file has the correct permissions (usually 600) and that it matches the public key on your device.
Best Practices for IoT SSH
To ensure a smooth and secure experience with IoT SSH on AWS, follow these best practices:
Use Strong Passwords
While SSH key pairs are recommended, if you're using passwords, make sure they're strong and unique. Avoid using common passwords or phrases.
Regularly Update Software
Keeping your devices and software up to date is crucial for security. Regular updates patch vulnerabilities and ensure that your devices are protected against the latest threats.
Monitor Logs
Regularly monitoring your SSH logs can help you detect and respond to potential security threats. AWS CloudWatch can be used to monitor and analyze your logs in real time.
Real-World Applications
IoT SSH access on AWS has a wide range of real-world applications across various industries. Here are a few examples:
Smart Agriculture
In the agriculture industry, IoT devices are used to monitor soil moisture, temperature, and other environmental factors. SSH access allows farmers to remotely manage these devices and make data-driven decisions to optimize crop yield.
Industrial IoT
In industrial settings, IoT devices are used to monitor machinery and equipment. SSH access enables engineers to perform remote diagnostics and maintenance, reducing downtime and increasing efficiency.
Smart Cities
Smart cities rely on IoT devices to manage traffic, lighting, and other infrastructure. SSH access allows city officials to monitor and manage these devices, ensuring that everything runs smoothly.
Future of IoT SSH on AWS
The future of IoT SSH on AWS looks bright. As more devices become connected, the demand for secure and efficient management solutions will only increase. AWS continues to innovate, introducing new features and services to enhance the IoT experience.
Some trends to watch out for include:
- Edge computing: Processing data closer to the source to reduce latency and improve performance.
- AI and machine learning: Using AI to analyze IoT data and make predictions, enabling smarter decision-making.
- 5G connectivity: Faster and more reliable connectivity will revolutionize how IoT devices are managed and accessed.
Conclusion
So, there you have it, folks! IoT SSH access on AWS is a powerful tool that can help you manage your IoT devices securely and efficiently. From setting up your environment to troubleshooting issues, this guide has covered everything you need to know.
Remember, security is key when it comes to IoT devices. By following best practices and leveraging AWS's robust security features, you can ensure that your devices remain safe from threats.
Now, it's your turn to take action. Whether you're setting up your first IoT device or managing a large-scale deployment, the knowledge and tools are at your fingertips. So, what are you waiting for? Get started today and unlock the full potential of IoT SSH on AWS!
Feel free to leave a comment or share this article if you found it helpful. And don't forget to check out our other articles for more tech insights and tips. Happy coding, and see you in the cloud!